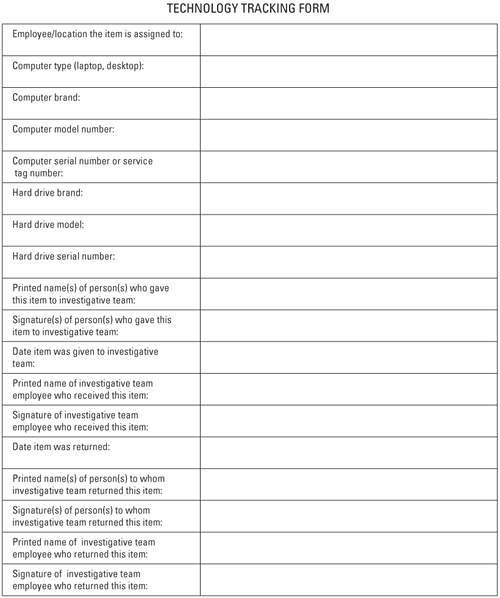
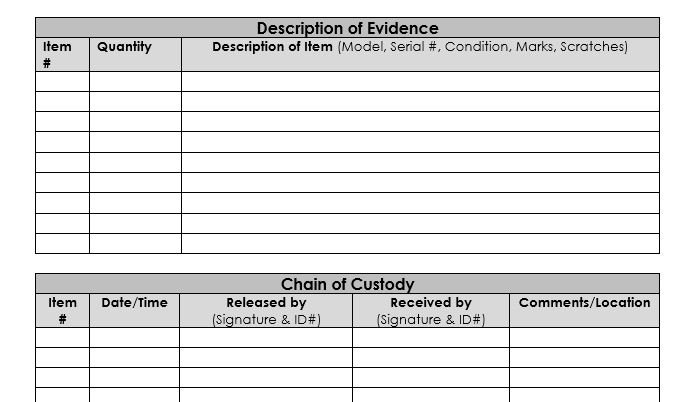
Evidence Collection and Chain of Custody | The Role of Computer Forensics in Stopping Executive Fraud | InformIT
Computer Forensics: A Linux Case Study Applied to Pedophilia Crime Investigation in Brazil. - Document - Gale Academic OneFile
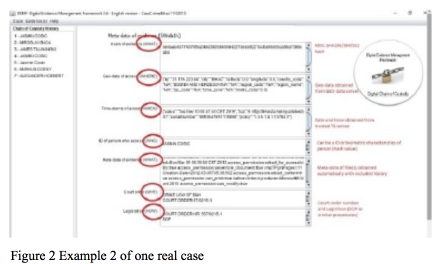
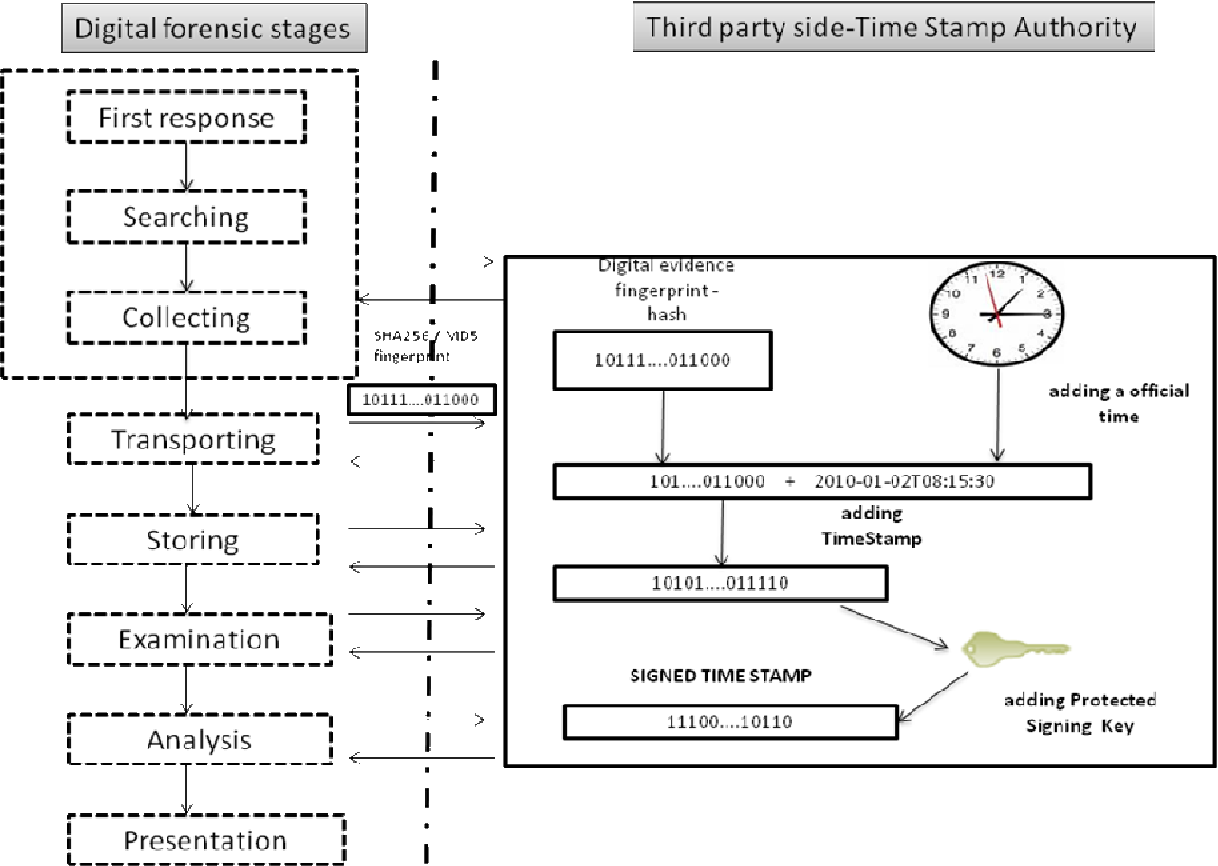
The Necessity Of Developing A Standard For Exchanging A Chain Of Custody Of Digital Evidence Data - Forensic Focus

Improving Chain of Custody in Forensic Investigation of Electronic Digital Systems | Semantic Scholar

Blockchain for Modern Digital Forensics: The Chain-of-Custody as a Distributed Ledger | SpringerLink

COMPUTER FORENSICS: CHAIN OF CUSTODY | NASSCOM Community | The Official Community of Indian IT Industry






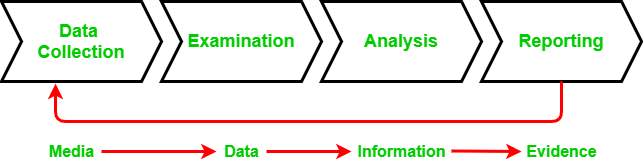


![PDF] Digital Chain of Custody: State of the Art | Semantic Scholar PDF] Digital Chain of Custody: State of the Art | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9e8a1f74a9dc68ce2f475c42fb42f47f3d7a955e/3-Figure1-1.png)