What is Computer Hacking? - Definition, Prevention & History - Video & Lesson Transcript | Study.com

Computer Intrusion Detection and Network Monitoring: A Statistical Viewpoint (Information Science and Statistics): Marchette, David J.: 9780387952819: Amazon.com: Books







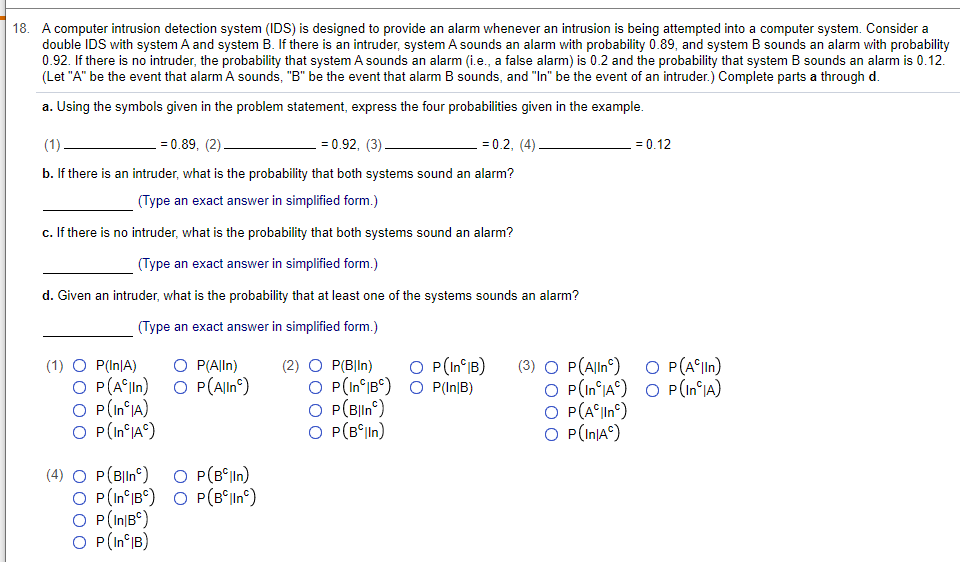












![PDF] Classification and detection of computer intrusions | Semantic Scholar PDF] Classification and detection of computer intrusions | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cfe2a9bad529af7427c8f67b569913b5c7c5112b/33-Figure2.1-1.png)