Faceless hacker at work with ROOTKIT VIRUS inscription, Computer security concept Stock Photo - Alamy
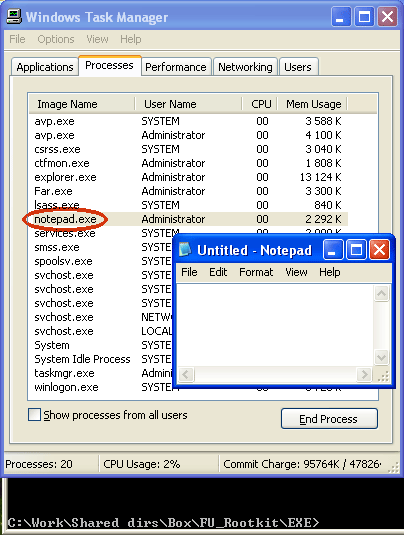
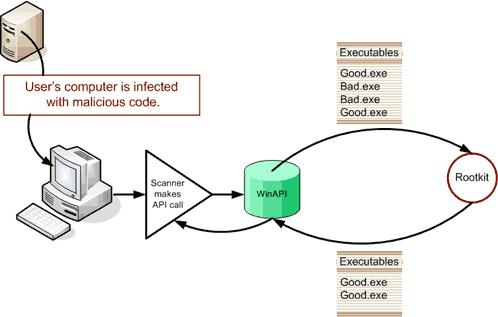
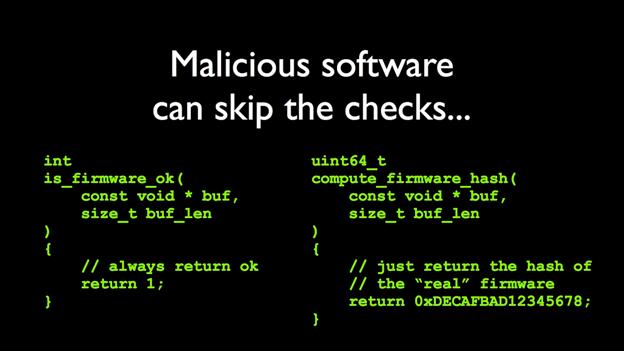
Rootkit Malware :More than a just virus, a Rootkit is a set of malicious software that is considered the most troublesome since it is also the hardest to remove from a computer